As explained in the previous post, clustering is categorizing set objects according to the similarity factor and there were three main categories. In this post the types of clustering is discussed.
There are two main types of clustering: Hierarchical and Partitional. In Hierarchical type what it does is arranging the elements according to an hierarchy whereas partitional, partitions the elements into groups.
In hierarchical type, it consists of two methods again, Bottom-up and Top-down. In top down, it categorize the total set in to two and then the each result will continue doing that according to a similarity value. In bottom up it makes couples according to the similarity. This is a very expensive method since it involves events with each and every data. These similar couples will make a hierarchy and hence called bottom up hierarchy.
The next type, partitional will partition the total element set to the clusters. The main difference is user input about the number of clusters is required here which will make it feasible to define any number of clusters. Randomly placed elements will be moved towards the center of the clusters in the process of finding the ideal cluster. This method increase the intra cluster concentration since every element moves to the center.
Gausian matrix model (GMM) is another method of doing that which eventually falls inside partitioning type.
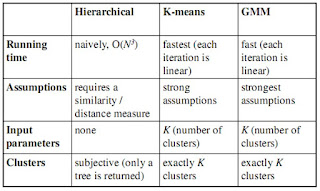
Following is a comparison of these three methods..